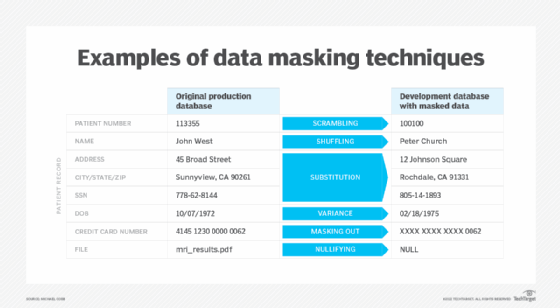
Amazon.com: Adult Kids Cloth Face Mask Computer Science Programmer Coder Nerd Code Gift Dust Masks Reusable Balaclava for Outdoor Black : Clothing, Shoes & Jewelry

Classic Hacker Mask - Computer Science Stud Framed Print Poster Wall or Desk Mount Options - Walmart.com

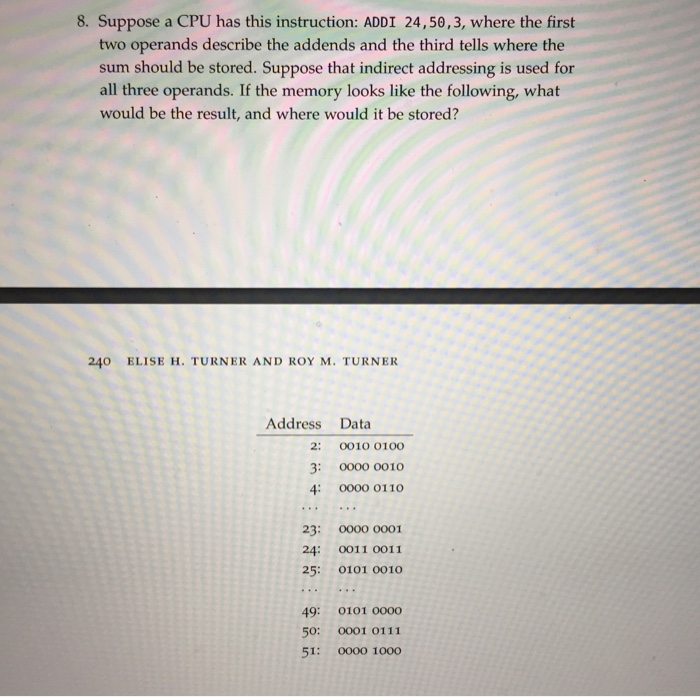
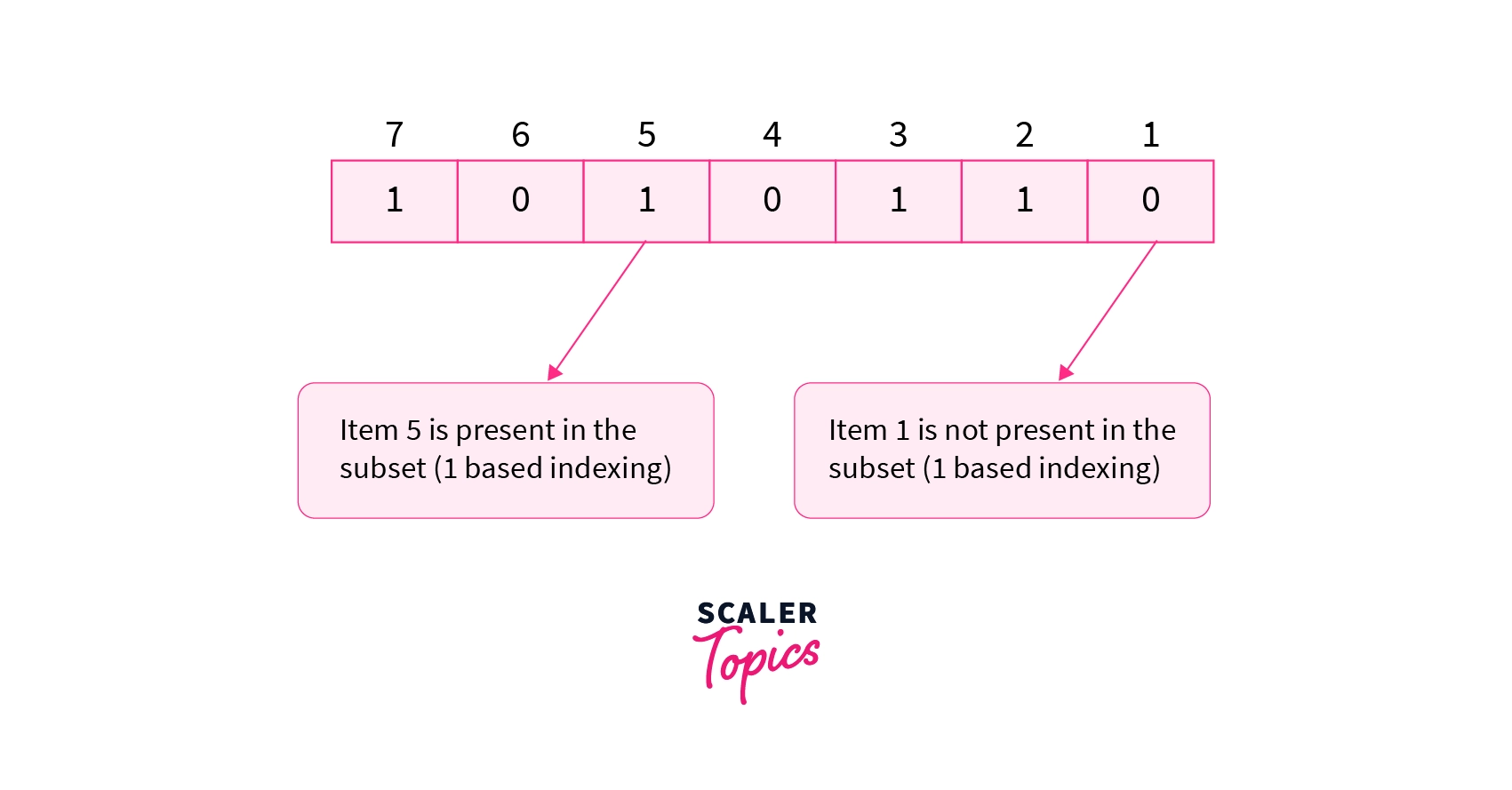
Computer Science: A Structured Programming Approach Using C1 14-4 Masks In many programs, bits are used as binary flags: 0 is off, and 1 is on. To set. - ppt download
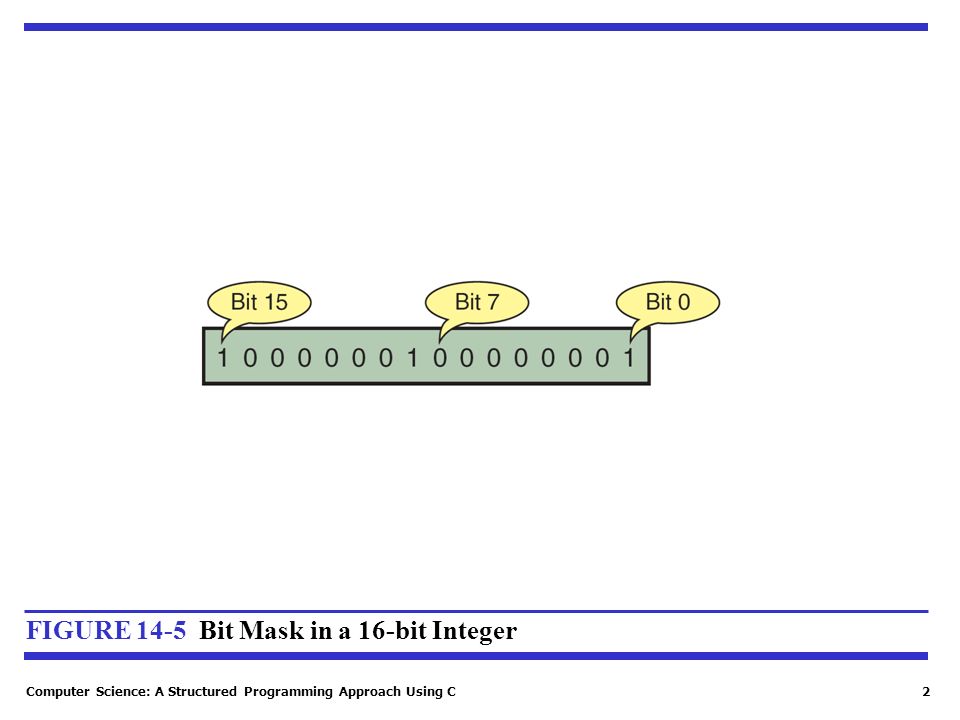
Computer Science: A Structured Programming Approach Using C1 14-4 Masks In many programs, bits are used as binary flags: 0 is off, and 1 is on. To set. - ppt download