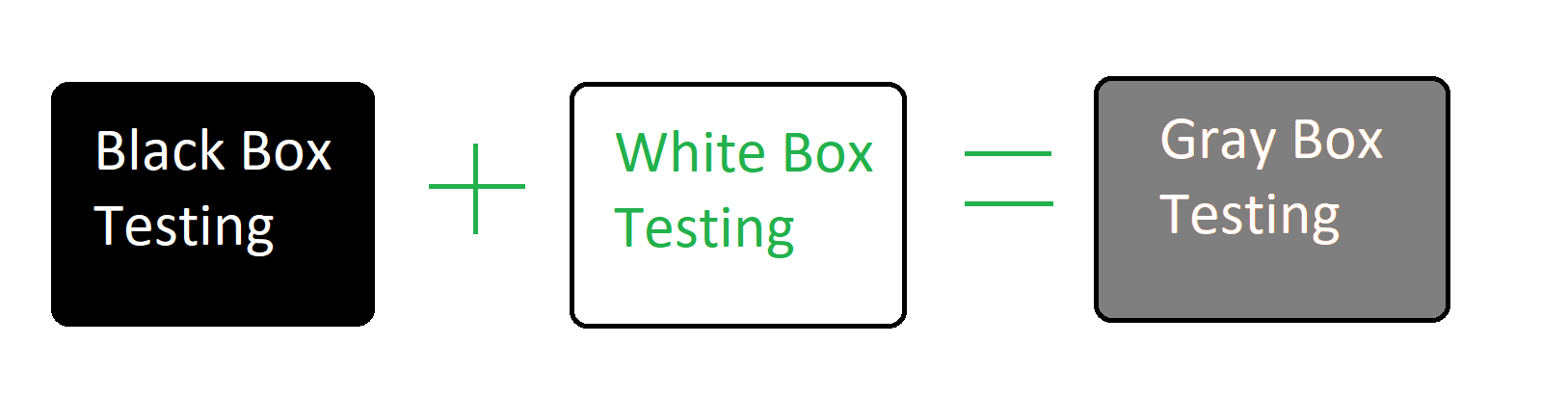
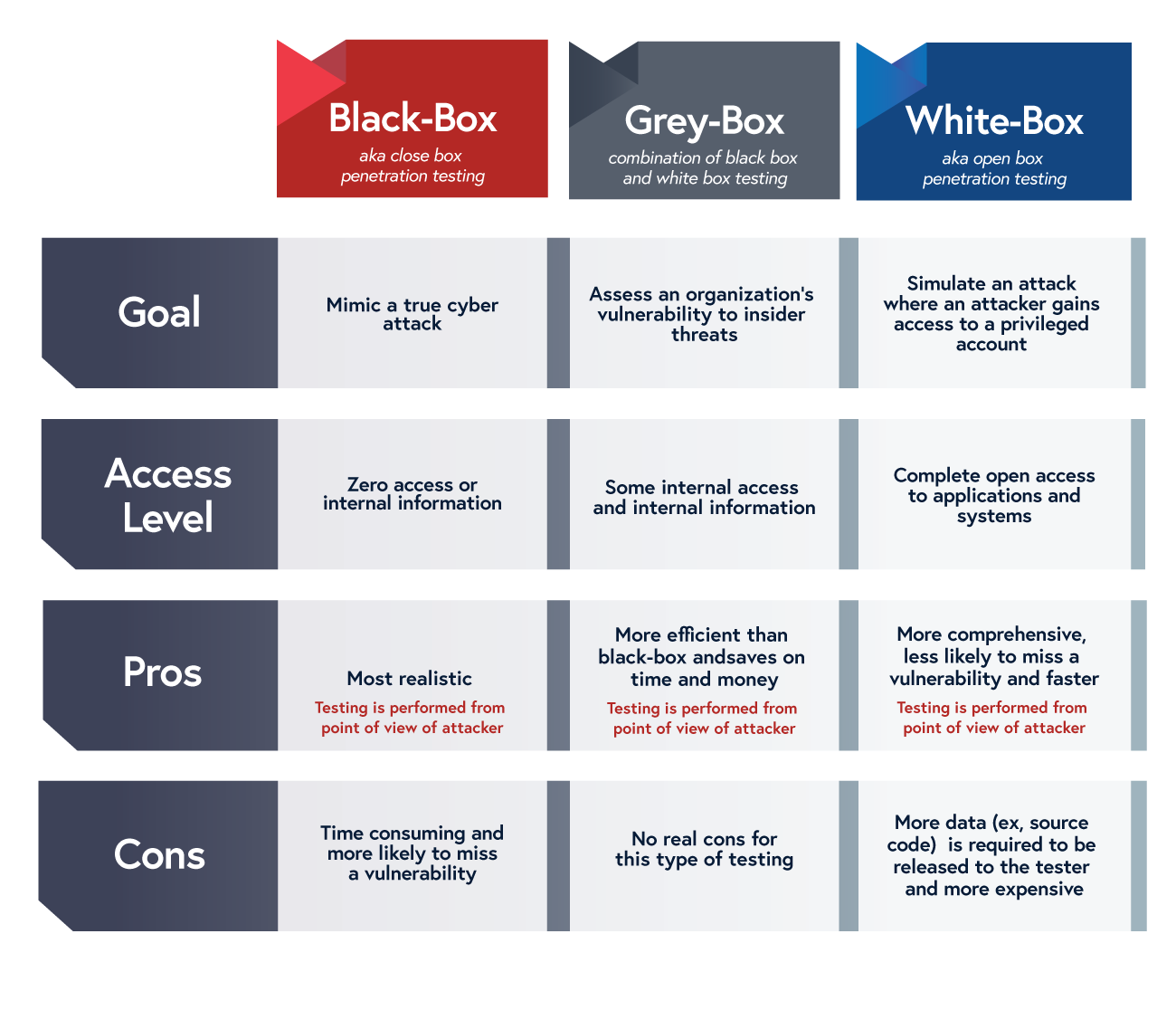
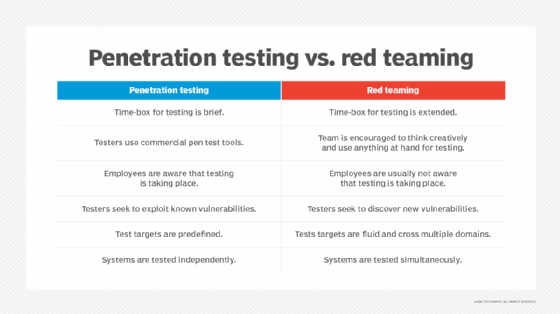
Engagment, sans Institute, Red team, software Performance Testing, white Box, Penetration test, cyberwarfare, Threat, Methodology, software Testing | Anyrgb
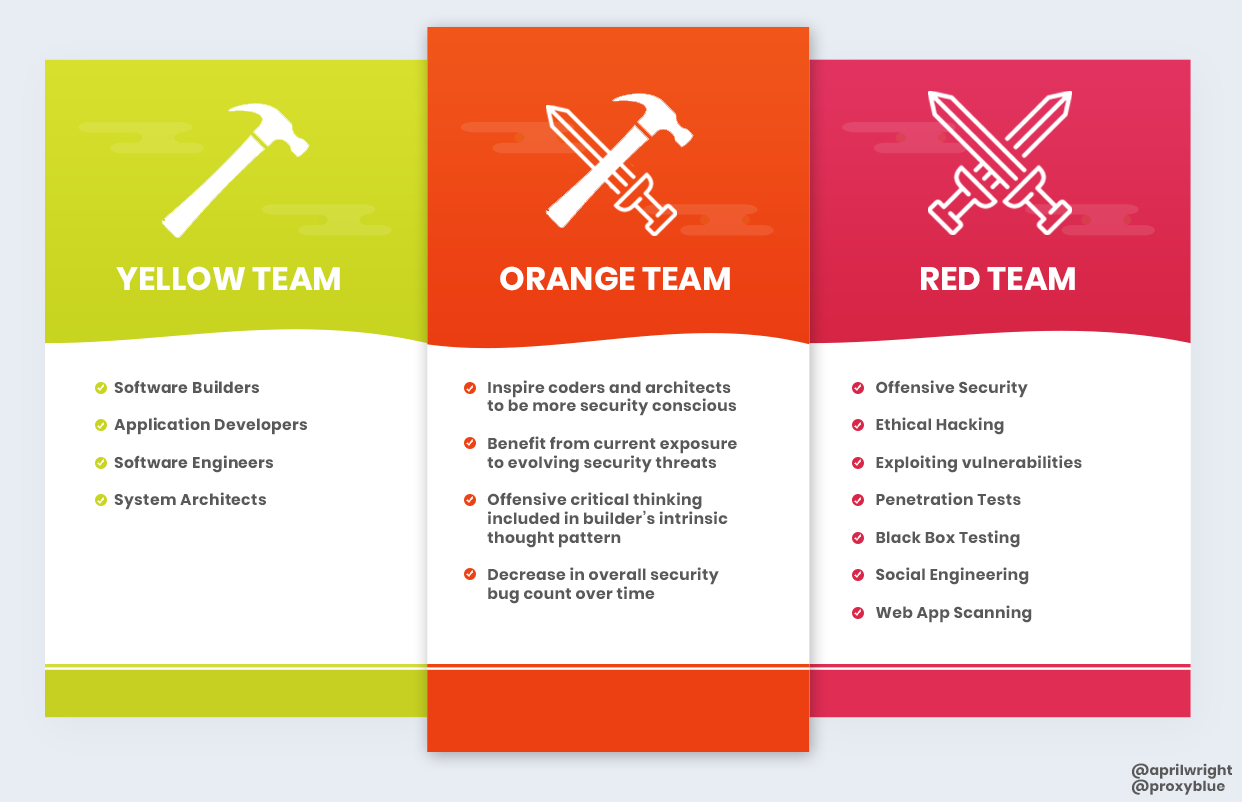
Introducing the InfoSec colour wheel — blending developers with red and blue security teams. | HackerNoon
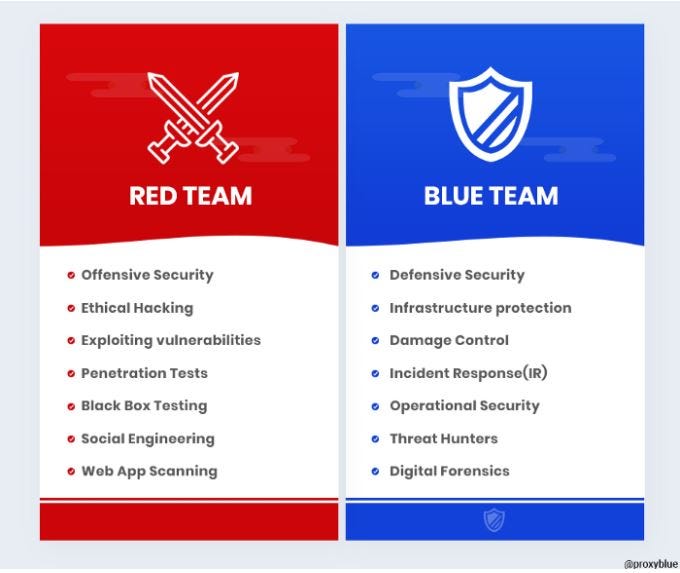
Cybersecurity Red Team Guide. My first blog was on the Blue Team side… | by Joshua Speshock | Medium